DevSecOps Essentials
By reading these notes, you will gain knowledge tailored to your role, whether you are a beginner or practitioner focusing on technical foundations or a manager looking to master DevSecOps leadership and strategy.
Note – This page contains a complete summary of the topics. To learn more about each topic, click on the (
Expand), Topic-Heading, Image, or ‘Click Here’ hyperlink.
Before reading this document, please read DevOps Essentials.
Complete DevOps Summary in One
1. Foundations and Culture
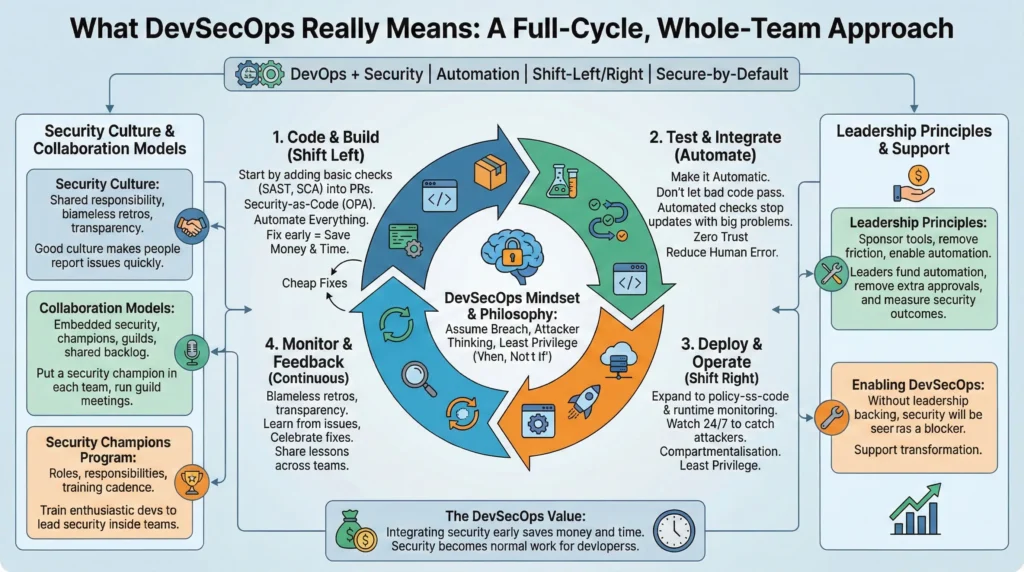
| Subject | Key Topics | Notes |
|---|---|---|
| What DevSecOps Really Means | DevOps + Security, automation, shift-left/right, secure-by-default | DevSecOps means adding security to every state and step of software development. Security done late is expensive; integrating security early saves money and time. Start by adding basic checks (SAST, SCA) into PRs, then expand to policy-as-code and runtime monitoring so security becomes normal work for developers. |
| DevSecOps Mindset and Philosophy | Assume breach, attacker thinking, least privilege | A mental model used by teams to design safer systems. If teams expect attacks, they design systems to reduce damage. Teach teams to assume “when, not if” for breaches; adopt least privilege, compartmentalisation, and automation to reduce human error. |
| Security Culture | Shared responsibility, blameless retros, transparency | Ways teams talk, act and reward around security. Good culture makes people report issues quickly and learn from them. Run blameless postmortems, create security champions, and celebrate fixes; avoid blame to encourage reporting. |
| Leadership Principles | Sponsor tools, remove friction, enable automation | How leaders support DevSecOps transformation. Without leadership backing, security will be seen as a blocker. Leaders fund automation, remove extra approvals, and measure security outcomes, not just ticket counts. |
| DevSecOps Principles | Security-as-code, zero trust, automate everything | Core rules that guide all decisions. These principles keep security consistent as systems grow. Convert policies to code (like OPA), apply least privilege, and automate checks as part of CI/CD. |
| Collaboration Models | Embedded security, champions, guilds, shared backlog | Practical ways teams share security work. Collaboration reduces friction and speeds fixes. Put a security champion in each team, run regular cross-team security guild meetings and keep security tasks in the same backlog as feature work. |
| Security Champions Program | Roles, responsibilities, training cadence | Program to train developer volunteers to lead security inside teams. Champions scale security knowledge across many teams. Pick enthusiastic devs, give them training, simple checklists, and time to help their team with threat modelling and code reviews. |
2. Secure SDLC and Application Security
| Subject | Key Topics | Notes |
|---|---|---|
| Secure SDLC (SSDLC) | Requirements → design → code → build → test → deploy → operate | A software life cycle that embeds security steps. It reduces production vulnerabilities and supports compliance. Add security tasks at each stage: threat model during design, SAST/SCA during build, DAST before release and monitoring in production. Track evidence for audits. |
| Secure Coding Practices | Input validation, output encoding, safe libs, OWASP Top 10 | Developer rules to avoid common bugs. Most incidents come from simple coding mistakes. Teach developers the OWASP Top 10; add linters; create secure helper libraries; use parameterized queries and whitelist validation. |
| Code Review for Security | AuthZ checks, data handling, secret checks, migration scripts | Security-focused checklist inside code reviews. Human review catches logic and context problems that tools miss. Add a security section to PR templates, require at least one reviewer trained in the checklist, and refuse merges until security items are resolved. |
| Threat Modelling | STRIDE, DFDs, attack surface, mitigations | Structured exercise to find likely attacks. Prevents expensive fixes later by solving architectural risks first. Draw a simple data flow diagram, list assets and threats, and convert top risks to stories assigned to devs. Repeat when architecture changes. |
| Application Security Layers | SAST, DAST, SCA, runtime controls, AuthN/AuthZ | Multiple defensive layers for applications. Different tools catch different problems; layering increases coverage. Implement SAST on PRs, SCA on merge, DAST in staging, and runtime monitors in production. Log all findings into one ticketing queue for triage. |
| SAST (Static Analysis) | PR checks, IDE plugins, triage of false positives | Tool-based scanning of source code for insecure patterns. Catches issues early and cheaply. Add SAST to pre-merge checks, tune rules to reduce noise, teach devs how to fix common findings, and prevent merges for high severity issues. |
| SCA (Software Composition Analysis) | CVE alerts, license checks, auto-upgrade PRs | Scans third-party libraries for known vulnerabilities. Most production risks come from vulnerable dependencies. Enable dependency scanners, create policies for auto-PRs for patches, and maintain a backlog for risky updates that need human testing. |
| Secrets Management | Vaults, secret rotation, OIDC, ephemeral creds | Secure storage and rotation of credentials and tokens. Stolen secrets lead to major breaches. Use a vault, never commit secrets to Git, use short-lived tokens via OIDC, and scan commits and logs for accidental secrets. |
| API Security | AuthN/AuthZ, BOLA prevention, schema validation, rate-limits | Protecting APIs that expose data and functionality. APIs are a top target for data theft and abuse. Validate inputs, enforce strict authorization checks, use API gateway patterns for rate limiting and monitoring, and adopt OWASP API Top 10 mitigations. |
| Business Logic Security | State validation, workflow correctness, abuse cases | Defend against attacks that misuse valid functionality. Automated scanners rarely find logic flaws. Map business workflows, create abuse-case tests, simulate attacker flows, and add dedicated logic tests in CI. |
3. CI/CD and Pipeline Security
| Subject | Key Topics | Notes |
|---|---|---|
| CI/CD Pipeline Security | Isolated runners, least privilege, signing, SBOM | Controls and architecture to make pipelines safe. Pipeline compromise allows attacker to push malicious builds. Use ephemeral or isolated runners, give pipelines only needed rights, enforce artifact signing and SBOM generation, and store pipeline logs for audit. |
| Pipeline Security Metrics | Signed artifact %, scan coverage, failed gates | KPIs to measure pipeline security. Metrics show gaps early and justify investment. Track how many builds are signed, percent of images scanned, and rate of failing security gates; set targets and report to leadership. |
| CI/CD Architecture Security | Ephemeral runners, sandbox builds, reproducible builds | Design principles for a secure build system. Well-designed CI limits blast radius and prevents tampering. Use ephemeral runners, run builds in sandboxes, enable reproducible builds so artifacts can be verified later. |
| Artifact and Registry Security | Immutable registry, RBAC, quarantine, retention | Protect the storage of built artifacts like Docker images. Unsafe registries allow distribution of malicious images. Make registries immutable for published images, use RBAC, quarantine suspicious builds, and maintain retention policies. |
| Software Supply Chain Security | SBOM, SLSA levels, provenance, cosign | Practices to secure every step from source to deployment. Attacks targeting dependencies or build systems can poison many apps. Generate SBOMs for every build, sign artifacts, adopt SLSA recommendations, and keep provenance records for audits. |
| GitOps Security | Signed manifests, secure controllers, reconciliation policies | Git-driven deployment model with added security. Git becomes the source of truth ensure it is protected and controllers follow policies. Sign manifests, lock CI/CD tokens, harden controllers (ArgoCD/Flux) and use admission rules to prevent unsafe changes. |
4. Infrastructure as Code (IaC) and Cloud Security
| Subject | Key Topics | Notes |
|---|---|---|
| IaC Security | Terraform/CloudFormation scanning, policy-as-code (OPA), misconfig detection | Scanning and policy for infrastructure templates. Misconfigured IaC leads to widely-exposed resources. Run policy checks in PRs, block public S3, require encryption by default, and apply OPA/Kyverno policies in CI. |
| Cloud Security Basics | IAM, VPC design, KMS, cloud logging, WAF | Core cloud controls across AWS/Azure/GCP. Proper identity and network design prevent lateral movement. Apply least privilege IAM, segregate workloads into VPCs/subnets, enable KMS for encryption, and centralize logs (CloudTrail/CloudWatch/Stackdriver). |
| Serverless Security | Function IAM, event validation, runtime limits, secrets handling | Security practices for serverless (Lambda, Functions). Functions often have broad triggers and permissions. Limit function permissions, validate event payloads, avoid long-lived secrets, and monitor invocations for anomalies. |
| Third-party and SaaS Security | Vendor assessments, token lifecycle, contract clauses | Manage risk coming from external services. Third-party compromise can directly impact your systems. Run vendor risk assessment, use short-lived tokens, enforce contract security clauses and monitor third-party activity. |
| Hardware-backed Key Security | CloudHSM, BYOK, envelope encryption, key rotation | Use hardware modules for storing keys. HSMs protect keys from software attacks and insider threats. Use KMS/HSM for critical keys, plan key rotation, and restrict who can request unwrap operations. |
5. Container Security
| Subject | Key Topics | Notes |
|---|---|---|
| Container Build Security | Multi-stage Docker builds, minimal images, remove dev tools, non-root user | Best practices while building container images. A smaller and clean image reduces vulnerabilities and attack surface. Use multi-stage builds to exclude build tools from final image, run as non-root, scan images for vulnerabilities, and store SBOM for each image. |
| Container Runtime Security | seccomp, AppArmor/SELinux, drop capabilities, eBPF monitoring (Falco/Cilium) | Controls that protect running containers. Runtime protections detect or prevent container escape and suspicious actions. Apply restrictive seccomp profiles, enable AppArmor/SELinux, drop unnecessary Linux capabilities, and install a runtime detector like Falco. |
| Container Supply Chain Security | Signed base images, private registries, vulnerability gating | Ensure images come from trusted sources and are safe. Attackers can poison base images or caches. Maintain a trusted base image library, sign images with cosign, block unscanned images from deploy and periodically re-scan stored images. |
6. Kubernetes Security
| Subject | Key Topics | Notes |
|---|---|---|
| Kubernetes Core Security | RBAC, NetworkPolicy, Namespaces, PodSecurity, resource limits | Basic hardening of a Kubernetes cluster. Misconfigured clusters expose secrets and controls. Use RBAC for least privilege, separate workloads by namespaces, enforce network policies to limit traffic and apply PodSecurity standards to disallow running as root. |
| Admission Control and Policy Enforcement | OPA Gatekeeper, Kyverno, validating and mutating webhooks | Prevent unsafe resources from being created. Admission controllers act before workloads run, stopping insecure configs. Add policies that enforce image signatures, disallow hostPath, require resource limits, and deny privileged containers. |
| Service Mesh Security | Istio/Linkerd, mTLS, SPIFFE identity, traffic policies | Secure service-to-service communication and control. Service meshes add encryption and identity for microservices without changing app code. Enable mTLS, issue per-service identities, limit allowed routes and monitor mesh logs for anomalies. |
7. Runtime Security and Observability
| Subject | Key Topics | Notes |
|---|---|---|
| DAST / IAST / RASP | OWASP ZAP, Burp, Contrast Security, runtime blocking | Dynamic scanners and runtime protection. Some vulnerabilities show only at runtime or under specific inputs. Run DAST against staging, use IAST in test runs for better coverage, and deploy RASP for critical apps to block attacks in production. |
| Monitoring and Logging | Centralized logs, Prometheus, Grafana, traces, SIEM | Observability and telemetry collection. Logs and metrics help detect incidents early and speed up investigations. Centralize logs, use structured logging, set meaningful alerts and correlate logs with traces during investigations. |
| Automated Response (SOAR) | Playbooks, auto-blocks, ticket creation, runbooks | Automation of routine incident responses. Automation reduces response time and human load. Create playbooks that block malicious IPs, rotate compromised keys, and create tickets for human follow-up when needed. |
| XDR for Cloud Apps | SIEM + EDR + NDR signals, unified triage | Extended detection combining multiple signal types. Single-source solutions miss cross-layer attacks. Integrate endpoint, network and cloud logs into a single platform to correlate suspicious sequences and speed up response. |
8. Identity, Access Control and Zero Trust
| Subject | Key Topics | Notes |
|---|---|---|
| IAM Deep-Dive | RBAC, ABAC, PBAC, JIT access, service accounts | Deep look at identity controls across systems. Identity is the main control point; misconfigurations cause large breaches. Apply least privilege, use attribute-based access where possible, enable JIT for administrators and monitor service accounts closely. |
| Zero Trust Architecture | Continuous verification, device attestation, micro-segmentation | Security model that trusts no implicit network boundary. In cloud and distributed apps, perimeter is gone; verifying everything prevents lateral movement. Implement identity checks everywhere, use mTLS and network segmentation, and monitor policy compliance continuously. |
| Secrets Sprawl Prevention | Detect leaked keys, secret age, elimination of duplicates | Ongoing program to reduce leaked or stale secrets. Old or duplicated secrets multiply risk. Scan repos and logs for secrets, replace secrets with identity-based access, and enforce automatic rotation and removal policies. |
9. Governance, Compliance and Maturity
| Subject | Key Topics | Notes |
|---|---|---|
| Compliance and GRC | ISO 27001, SOC 2, PCI-DSS, GDPR, policy-as-code | Ensuring organisation follows legal and industry rules. Compliance avoids fines and builds trust with customers. Map controls to automated checks in CI, maintain evidence like SBOMs and pipeline logs, and run periodic audits. |
| DevSecOps Metrics | MTTR, MTTD, vulnerability backlog, policy violation rates | Measurement of security health and process success. Metrics help prioritize work and show ROI to leadership. Track MTTR for critical vulnerabilities, percent of PRs scanned, and policy violations over time. Use dashboards to show trends. |
| DevSecOps Maturity Model | Levels 1–5 (Ad-hoc → Elite) | Roadmap to grow DevSecOps capabilities. Organisations need a practical plan to improve. Assess current level, pick next level goals (automation, SBOM, runtime protection) and measure progress quarterly. |
| Enterprise Operating Model | RACI, governance committees, budgeting, central vs embedded teams | How to structure security across many teams. Scaling DevSecOps requires clear ownership and funding. Define RACI for security tasks, form a governance committee, fund shared platform teams and keep an embedded security presence in product teams. |
10. Frontend, Mobile and API Security
| Subject | Key Topics | Notes |
|---|---|---|
| Frontend Security | CSP, CSRF, XSS, secure cookies, CSP headers | Techniques to protect browser-based code and users. Attacks on the browser can steal sessions and data. Set strict CSP, use secure SameSite cookies, escape and sanitize user input, and avoid storing sensitive tokens in localStorage. |
| Mobile App Security | APK/IPA signing, keystore protection, jailbreak/root detection, secure storage | Securing mobile apps from tampering and data theft. Devices are untrusted and apps run in hostile environments. Use secure signing and keystore management, obfuscate code, detect jailbroken devices and encrypt local storage. |
| API Abuse Protection | Rate limiting, bot detection, CAPTCHA, usage analytics | Controls to stop misuse of APIs (not just security bugs). Attackers can automate abuse like credential stuffing or scraping. Implement rate limits, use behaviour-based detection, throttle suspicious requests and use CAPTCHAs where human verification is needed. |
11. Advanced Security Engineering
| Subject | Key Topics | Notes |
|---|---|---|
| Business Logic Security | Abuse-cases, state validation, race condition prevention | Focus on application-specific misuse that automated tools miss. Logic bugs can lead to large monetary or privacy loss. Map out important flows (checkout, refunds), write targeted tests and run adversarial scenarios in CI. |
| Red / Blue / Purple Teaming | Manual pentest, ATT and CK mapping, collaborative testing | Practice attack and defence exercises. Real attackers often use creative methods not detected by scanners. Run periodic red team engagements, map findings to MITRE ATT and CK, and use purple team sessions to improve detections. |
| Security Chaos Engineering | Fault injection, failure tests, detection verification | Intentionally breaking controls to verify detection and response. Proves systems work in real failures. Run safe experiments (e.g., disable a detection rule temporarily) and ensure alerts and runbooks trigger correctly. |
| Automated Red Team Tests | CI-based small attacks (Atomic Red Team) | Small safe attack simulations in CI. Provides continuous validation of detection. Add a set of harmless atomic tests that exercise known attacker techniques in a sandbox and check that sensors alert. |
| Event-driven Security Automation | Lambda playbooks, Security as Code, auto-remediation | Automate common remediation steps on alerts. Speed reduces attacker dwell time. Build serverless playbooks that get triggered by critical alerts for example, rotate credentials or block IPs and log each action for audit. |
12. Operations, Disaster Recovery and Developer Experiance
| Subject | Key Topics | Notes |
|---|---|---|
| Disaster Recovery and Business Continuity | Backups, restore drills, failover, plan testing | Plans and processes to recover from major incidents. Downtime and data loss impact customers and revenue. Create tested backups, rehearse restores regularly, document RTO/RPO, and ensure secrets are rotated after failover. |
| Developer Enablement | Golden templates, self-service infra, secure libraries | Tools and resources to help developers write secure code easily. Low-friction tooling increases compliance and speed. Provide starter repos, secure CI templates, pre-approved infra modules and office hours for help. |
| Developer Experience (DevEx) | Low friction security, fast feedback, helpful errors | Make secure choices the easy ones. If security is hard, devs will find shortcuts. Reduce developer wait times for scans, give helpful error messages and integrate security into IDEs and PRs. |
| Mobile Distribution Security | Signed APK/IPA, revocation, store controls | Protecting app delivery and updates. Tampered apps can cause fraud or data leaks. Use secure signing, monitor app store releases, plan forced upgrades and maintain revocation methods for compromised builds. |
13. Data, Storage and Database Security
| Subject | Key Topics | Notes |
|---|---|---|
| Database Security | Encryption at rest, query firewall, role-based db access, auditing | Controls to protect stored data. Databases hold PII and business data that attackers want. Use DB-level encryption, limit DB user privileges, enable auditing for sensitive actions, and monitor slow or unusual queries for signs of abuse. |
14. AI/ML + Future Security
| Subject | Key Topics | Notes |
|---|---|---|
| AI/ML/LLM Security | Data poisoning, prompt injection, model theft, model signing | Protecting machine learning pipelines and models. Attacks here can corrupt models or leak training data. Validate training data, control access to model registries, sign models, and sanitise prompts and inputs before passing to LLMs. |
| Privacy Engineering | DPIA, data minimization, tokenization, PII handling | Designing systems that respect user privacy and compliance. Privacy violations cause legal and reputational damage. Classify data, minimize storage of PII, use tokenization and display only necessary data, and run DPIAs for high risk features. |
| Quantum-Safe Cryptography | Post-quantum algorithms, hybrid crypto, migration planning | Preparing cryptography for future quantum threats. Future quantum computers could break current encryption. Monitor NIST PQC standards, plan hybrid key exchanges and identify critical assets that must be migrated first. |
15. Monorepo, Build and Large Scale Systems
| Subject | Key Topics | Notes |
|---|---|---|
| Monorepo Build Security | Hermetic builds, dependency graphs, distributed cache protection | Secure build practices for large mono-repositories. Large repos need deterministic builds and careful dependency control. Use hermetic build tools (Bazel/Pants), sandbox builds, protect distributed caches and verify dependency provenance. |
16. Supply Chain and Third Party Risk
| Subject | Key Topics | Notes |
|---|---|---|
| Third-party Supply Chain Security | Vendor SBOMs, contractual security requirements, risk rating | Managing risk from vendors and open-source. A vendor compromise can cascade into your products. Request SBOMs from vendors, include security SLAs in contracts, rate vendors on security posture and limit direct access to sensitive data. |
Some important links for reference